Enhancing Access Control with Facial Recognition for Highly Secure Spaces.

In the realm of access control for highly secure spaces, such as bank vaults, laboratories, data centers, and government facilities, the need for advanced security measures is paramount. Traditional access methods like keys or keycards are no longer sufficient to safeguard these critical environments. This is where facial recognition technology emerges as a cutting-edge solution, revolutionizing access control with its accuracy, efficiency, and reliability. Let’s explore how facial recognition enhances security in highly secure spaces and examine specific examples like bank vaults, laboratories, and data centers. The Evolution of Access Control Access control systems have evolved significantly, transitioning from mechanical locks to digital solutions that leverage biometric technologies like facial recognition. Facial recognition stands out as a game-changing innovation, offering a seamless and robust method to authenticate individuals based on unique facial features. Enhancing Security in Bank Vaults Bank vaults house valuable assets and confidential information, requiring the highest level of security. Facial recognition technology ensures that only authorized personnel gain access to these restricted areas. Employees and security personnel can be swiftly verified through facial recognition at vault entrances, minimizing the risk of unauthorized access. Securing Laboratories with Facial Recognition Laboratories handling sensitive research and experiments rely on stringent access control measures. Facial recognition systems provide a secure and efficient way to manage access, maintaining a detailed record of personnel movement within the facility. Researchers can focus on their work with confidence, knowing that access to critical areas is closely monitored and controlled. Protecting Data Centers Data centers store vast amounts of critical information, making them prime targets for cyber threats. Access control is crucial to prevent unauthorized entry and protect sensitive data. Facial recognition technology enhances data center security by ensuring that only authorized personnel can access server rooms and control areas. This mitigates the risk of data breaches and unauthorized tampering. Advantages of Facial Recognition in Highly Secure Spaces. High Accuracy: Facial recognition systems accurately identify individuals based on unique facial features, minimizing the risk of unauthorized access. Streamlined Access: Employees can enter secure areas without the need for physical keys or access cards, enhancing convenience and efficiency. Real-time Monitoring: Facial recognition systems maintain detailed access logs, enabling real-time monitoring of personnel movement for enhanced security and accountability. Integration with Existing Systems: Facial recognition seamlessly integrates with existing access control systems, providing a scalable solution for highly secure spaces. Implementing Facial Recognition with Millennium Access Control Millennium Access Control specializes in deploying facial recognition technology for highly secure spaces. By partnering with Millennium, organizations benefit from: Expert Consultation: Millennium offers expert guidance on implementing facial recognition systems tailored to specific security requirements. Customized Solutions: Each deployment is customized to align with the unique needs and challenges of bank vaults, laboratories, data centers, and government facilities. Advanced Security Features: Millennium integrates advanced security features to enhance access control and protect highly sensitive areas. Conclusion Facial recognition technology is a transformative solution for enhancing access control in highly secure spaces. By leveraging this innovative technology, organizations can fortify security measures, streamline access, and ensure the protection of valuable assets and information. With the expertise of Millennium Access Control, implementing facial recognition becomes a seamless process, empowering organizations to safeguard their most critical environments with confidence. MGI is a scalable, hosted, access control platform that services any type of real estate. Our cloud-based solution allows managers and tenants to efficiently manage their physical security from anywhere while enhancing the experience and driving profitability.
Secure the Future with MIFARE Tokens on Campus.

In the dynamic realm of campus management and security, technology stands as a cornerstone, pivotal in ensuring both efficiency and safety. Among the array of technological advancements transforming access control and student identification in university and school campuses, one innovation shines brightly: the Mifare token. Understanding MIFARE Tokens MIFARE tokens are contactless smart cards or key fobs embedded with RFID technology, specifically powered by NXP Semiconductors’ MIFARE chips, which are embedded with encrypted data and can communicate wirelessly with compatible readers. These tokens enable secure and convenient access control, making them ideal for various applications within organizations. Advantages of MIFARE Tokens in Campus Settings Enhanced Security: MIFRAE tokens provide a higher level of security compared to traditional keys or magnetic stripe cards. The encrypted data stored on the tokens reduces the risk of unauthorized access and cloning, thereby safeguarding sensitive areas like dormitories, labs, and administrative offices. Convenient Access Control: With MIFARE tokens, students and staff can access designated areas seamlessly by simply tapping or waving their card near a reader. This eliminates the need for physical keys or manual checks, saving time and improving overall campus flow. Multi-functionality: MIFAREtokens can be programmed for various applications beyond access control. They can serve as campus IDs, library cards, meal cards for cafeterias, and even payment cards for vending machines or campus stores. This consolidation reduces the number of cards a student needs to carry and simplifies campus life. Real-time Tracking: Educational institutions can track the movement of students and staff using MIFARE tokens. This data can be useful for attendance monitoring, ensuring safety during emergencies, and optimizing campus operations. Customizable Features: MIFARE tokens offer flexibility in terms of programming and customization. Campuses can tailor the tokens to meet specific needs such as setting access permissions based on roles or scheduling temporary access for visitors. Cost-effective and Durable: These tokens are cost-effective over time as they reduce the expenses associated with replacing lost keys or reissuing ID cards. Additionally, MIFARE tokens are built to withstand daily wear and tear, making them durable for long-term use. Implementation in University and School Campuses Using MIFARE tokens in educational institutions involves integrating compatible readers and backend systems. Campus security personnel and administrators play a crucial role in configuring access rights, monitoring system performance, and issuing tokens to students and staff. Conclusion In conclusion, Mifare tokens are a game-changer for university and school campuses seeking to modernize their security and administrative systems. With their advanced security features, multi-functionality, and ease of use, Mifare tokens contribute to a safer, more efficient learning environment. As technology continues to evolve, educational institutions will undoubtedly rely on innovative solutions like Mifare tokens to meet the demands of today’s campus management challenges MGI is a scalable, hosted, access control platform that services any type of real estate. Our cloud-based solution allows managers and tenants to efficiently manage their physical security from anywhere while enhancing the experience and driving profitability.
Elevate Your Security: 3 Ways MIFARE Protects Growing Companies.

Security and efficiency are key pillars of success, and Mifare tokens help businesses elevate their game. But what exactly are Mifare tokens, and how can they make a difference? explore three ways Mifare tokens improve security and help growing companies run smoothly. Fortified Security Fortress Picture this: your company’s sensitive data, proprietary information, and valuable assets—are protected by a digital fortress impenetrable to would-be intruders. That’s the power of Mifare tokens. With advanced encryption technology and secure authentication protocols, Mifare tokens ensure that only authorized personnel gain access to your company’s premises, networks, and resources. Say goodbye to sleepless nights worrying about data breaches or unauthorized access—Mifare tokens have your back. Streamlined Operations, Seamless Experience Growing companies are like well-oiled machines, with every cog and gear working in perfect harmony. But what happens when one cog gets stuck? Chaos ensues. Mifare tokens act as the lubricant that keeps the machine running smoothly. With their contactless technology and easy-to-use interface, Mifare tokens streamline access control processes, reducing wait times and minimizing friction for employees, visitors, and clients. Whether it’s entering the office, accessing secure areas, or making cashless payments, Mifare tokens deliver a seamless experience that keeps your operations humming along. As your company grows, so do your security needs. But fret not—Mifare tokens are built to scale with you every step of the way. Whether you’re adding new employees, expanding to new locations, or integrating with other systems, Mifare tokens offer the flexibility and versatility to adapt to your evolving requirements. Say goodbye to cumbersome hardware upgrades or costly infrastructure overhauls—Mifare tokens make scalability simple, ensuring that your security infrastructure grows alongside your company. Contact Millennium Group Inc. by requesting a demo today and discover how Mifare tokens can transform your security infrastructure. In conclusion, Mifare tokens are more than just a piece of plastic—they’re a game-changer for growing companies looking to bolster security and streamline operations. With their fortified security features, streamlined user experience, and effortless scalability, Mifare tokens are the secret weapon that empowers businesses to thrive in today’s competitive landscape. So why wait? Elevate your security game with Mifare tokens and watch your company soar. Ready to leap? Let’s secure your success together. MGI is a scalable, hosted, access control platform that services any type of real estate. Our cloud-based solution allows managers and tenants to efficiently manage their physical security from anywhere while enhancing the experience and driving profitability.
Unlocking Security: Why you Need to Choose MIFARE Tokens for Keyfobs Over Proximity Cards

In access control, the choice of technology can significantly impact security, efficiency, and overall user experience. Whether safeguarding sensitive information or ensuring the safety of personnel and assets, having a robust access control system is essential. While proximity keyfobs have been a popular choice for many, there’s a compelling argument for transitioning to Mifare tokens for enhanced security and convenience. At Millennium Group Inc., we advocate for this innovative approach, and here’s why we believe you should make the switch. Firstly, Mifare tokens offer advanced encryption capabilities compared to traditional proximity keyfobs. With built-in AES encryption, Mifare tokens provide an extra layer of protection against unauthorized access and cloning attempts. This ensures that only authorized individuals can gain entry, mitigating the risk of security breaches and enhancing overall system integrity. Moreover, Mifare tokens boast greater versatility and functionality. Unlike proximity keyfobs, which typically have limited storage capacity, Mifare tokens can store a wealth of information, including access credentials, user data, and even financial transactions. This versatility opens up many possibilities, from integrating access control with other systems to facilitating secure payments and transactions within the organization. Additionally, Mifare tokens offer improved convenience and ease of use. With their contactless technology, users can effortlessly gain access with a simple tap or swipe, eliminating the need for physical insertion or contact with the reader. This not only speeds up the entry process but also reduces wear and tear on the access control system, leading to fewer maintenance issues and greater reliability over time. One of the key advantages of Mifare tokens is their versatility and flexibility. These tokens can store a wide range of information, including access credentials, biometric data, and even financial transactions, making them suitable for various applications beyond traditional access control. By leveraging Mifare tokens for keyfobs, organizations can streamline operations, simplify user authentication processes, and enable seamless integration with other systems such as time and attendance tracking or cashless payment solutions. Furthermore, Mifare tokens are highly scalable and future-proof. As technology continues to advance, having a flexible and adaptable access control solution becomes increasingly important. Mifare tokens provide the scalability to accommodate future expansions and upgrades, ensuring that your access control system remains relevant and effective in the long run. At Millennium Group Inc, we believe that access control is more than just a necessity—it’s an opportunity to elevate security, efficiency, and user experience. By embracing innovative solutions like MIFARE tokens for keyfobs, organizations can unlock a new level of control. By making the switch, you can future-proof your security infrastructure, streamline operations, and enjoy peace of mind knowing that your assets and personnel are protected by the latest advancements in access control technology. Millennium Group has several opportunities to help you change what you have to MIFARE. Contact Millennium Group Inc. by requesting a demo today and discover how Mifare tokens can transform your security infrastructure MGI is a scalable, hosted, access control platform that services any type of real estate. Our cloud-based solution allows managers and tenants to efficiently manage their physical security from anywhere while enhancing the experience and driving profitability.
Secure Spaces With Millennium Access Control And Visitor Management

In an era where security is paramount, businesses and organizations are constantly seeking advanced solutions to safeguard their spaces. One such indispensable tool is the integration of Millennium Access Control and Visitor Management systems, a dynamic duo that promises not just security, but peace of mind. Security is not just a necessity; it’s a foundation for trust and productivity. Whether it’s an office building, residential complex, or any public space, ensuring the safety of individuals and assets is paramount. Traditional security measures often need to catch up in the face of evolving threats, making it imperative to adopt advanced solutions The Foundation of Security: Millennium Access Control Modern Technology at Your Fingertips Millennium Access Control leverages cutting-edge technology to provide a robust foundation for security. Through advanced authentication methods, biometric recognition, and smart card systems, access is granted only to authorized individuals. This not only enhances the overall security posture but also streamlines the entry process. Real-time Monitoring and Reporting One of the key features of Millennium Access Control is its real-time monitoring capabilities. Security personnel can monitor access points, track movement within the premises, and receive instant alerts for any suspicious activities. This proactive approach enables swift responses to potential security threats. Integration for Seamless Operations Millennium Access Control is designed with integration in mind. It seamlessly integrates with other security systems, such as CCTV cameras and alarm systems, creating a cohesive security infrastructure. This interconnected approach ensures that all components work together harmoniously to provide comprehensive protection. Elevating Security with Visitor Management Precision in Guest Authentication Visitor Management takes security a step further by offering precise control over guest access. The system captures essential visitor information and validates their identity before granting entry. This meticulous authentication process ensures that only authorized individuals gain access to the premises. Efficient Check-in and Check-out Processes Gone are the days of cumbersome paper logbooks. Visitor Management streamlines the check-in and check-out processes, enhancing efficiency and minimizing wait times. The system maintains a digital record of visitor activity, making it easy to retrieve historical data when needed. Enhanced Emergency Preparedness In times of emergencies, every second counts. Visitor Management contributes to enhanced emergency preparedness by providing accurate information about the number and location of visitors within the facility. This knowledge empowers security teams to respond swiftly and effectively during critical situations. The Future of Secure Spaces Millennium Access Control and Visitor Management mark a paradigm shift in how we approach security. By leveraging advanced technology, streamlined processes, and real-time monitoring, these systems ensure that spaces remain secure without compromising on efficiency. The integration of these solutions creates a robust security ecosystem, setting a new standard for secure living and working environments. In conclusion, when it comes to securing spaces, the combination of Millennium Access Control and Visitor Management is unparalleled. It’s not just about controlling access; it’s about creating an environment where safety is non-negotiable. As we continue to embrace technological advancements, these solutions pave the way for a future where secure spaces are the norm, not the exception. MGI is a scalable, hosted, access control platform that services any type of real estate. Our cloud-based solution allows managers and tenants to efficiently manage their physical security from anywhere while enhancing the experience and driving profitability.
Rising to New Heights: Elevators and Why Millennium Elevator Access Control Takes the Lead

Elevators – those vertical movers that seamlessly transport us between floors, often overlooked but undeniably essential in our daily lives. In this blog, we’ll delve into the reasons elevators are crucial and explore why the Millennium Elevator Access Control stands out as a smart choice for enhanced security. The Elevator Advantage Elevators have become synonymous with modern convenience, effortlessly transporting us between floors with a simple push of a button. In bustling office buildings, residential complexes, and shopping centers, elevators streamline accessibility, making spaces more inclusive for people of all abilities. The time saved by elevators compared to stairs is invaluable, especially in our fast-paced lives. Besides being a convenience master, elevators are crucial for safety reasons. In the case of emergencies or medical issues, elevators provide a swift exit or entrance without the physical strain of stairs. They’re like the silent guardians of high-rises, ensuring everyone can move around effortlessly while maintaining safety standards. Why Elevators Matter: Accessibility: Elevators make spaces accessible to everyone, regardless of physical abilities. They promote inclusivity by ensuring that individuals with mobility challenges can navigate buildings effortlessly. Efficiency: Elevators save time and energy, providing a swift and efficient mode of transportation within multi-story structures. This is particularly crucial in busy environments where every minute counts. Safety: Elevators are designed with safety features to prevent accidents and ensure the well-being of passengers. With proper maintenance, elevators are among the safest modes of transportation. Now, let’s talk about why your elevator experience can reach new heights with Millennium Elevator Access Control. Imagine having the power to regulate and secure elevator access seamlessly. It’s not just about going up and down; it’s about doing it intelligently Automated Precision: Millennium Elevator Access Control takes the reins, ensuring that your elevator is not just a people-mover but a smart entity. With the ability to regulate the number of individuals in each elevator, the system ensures a comfortable and safe experience. It automatically manages the number of passengers, preventing that awkward “can you squeeze in?” scenario and unnecessary delays. Enhanced Security Measures: We’re not just talking about going up; we’re talking about going up safely. Millennium Elevator Access Control goes beyond conventional security measures. It actively monitors and manages access, providing a secure environment within elevators. This is particularly crucial in busy office buildings or high-security facilities. With advanced security features, our Elevator Access Control ensures that only authorized individuals have the golden ticket to the elevator party Seamless Integration: One of the standout features is its seamless integration capabilities. The system effortlessly blends into the existing infrastructure, minimizing disruptions during installation while maximizing security benefits. In a nutshell, elevators are more than just a means of transportation; they are integral to creating functional and accessible spaces. Choosing the right elevator access control system is equally important. With its innovative features, the Millennium Elevator Access Control emerges as a smart choice, ensuring not just mobility but also security in our vertical journeys. Elevate your space with Millennium – the pinnacle of intelligent elevator access control. MGI is a scalable, hosted, access control platform that services any type of real estate. Our cloud-based solution allows managers and tenants to efficiently manage their physical security from anywhere while enhancing the experience and driving profitability.
Unlock Maximum Access Control Potential With Integrated Video Surveillance
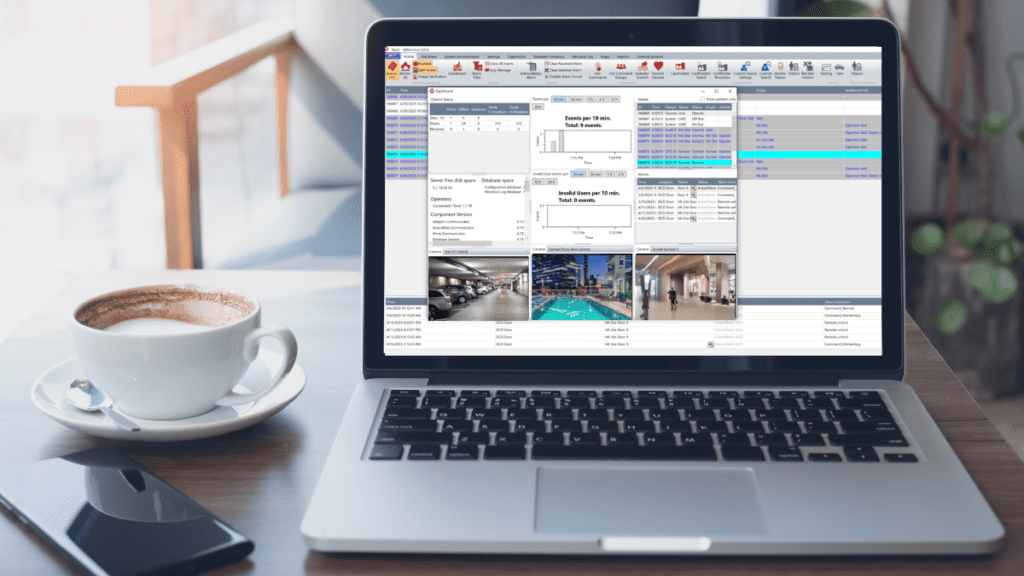
In today’s rapidly evolving world, ensuring the security and safety of our premises has become a paramount concern. Traditional security measures alone may not be enough to address the growing complexities of modern threats. That’s where the integration of video surveillance and access control systems comes into play. By combining these two powerful technologies, organizations can achieve heightened security, improved operational efficiency, and greater peace of mind. In this blog, we will delve into the reasons why integrated video surveillance with access control is not only good but also vital for comprehensive security solutions. Enhanced Situational Awareness: The integration of video surveillance and access control empowers organizations with a holistic view of their premises. By correlating access events with real-time video footage, security personnel can quickly respond to incidents, identify potential risks, and make informed decisions. This enhanced situational awareness enables proactive measures and timely interventions, significantly enhancing overall security levels. Accurate Identity Verification: Access control systems provide a valuable layer of security by restricting entry to authorized personnel. However, the integration with video surveillance adds an extra dimension of identity verification. By capturing video footage of individuals at access points, organizations can verify the authenticity of credentials and prevent unauthorized entry attempts. This powerful combination helps mitigate security breaches and strengthens access control effectiveness. Forensic Investigation and Evidence: In the unfortunate event of security incidents or breaches, the integration of video surveillance and access control plays a crucial role in forensic investigations. By correlating access events with recorded video footage, investigators gain valuable evidence for identifying culprits, understanding the sequence of events, and strengthening legal proceedings. This seamless integration simplifies the retrieval and analysis of relevant footage, saving time and resources during investigations. Operational Efficiency and Streamlined Processes: Beyond security benefits, the integration of video surveillance and access control systems brings notable operational advantages. Integrated systems allow for centralized management, eliminating the need for separate platforms and reducing complexity. Administrators can conveniently configure access permissions, monitor live video feeds, and generate comprehensive reports, all from a unified interface. This streamlined approach simplifies administrative tasks, enhances efficiency, and optimizes resource allocation. Scalability and Future-Proofing: The integration of video surveillance and access control systems offers scalability and future-proofing capabilities. As organizations grow or security requirements evolve, integrated systems can easily accommodate expansions and upgrades. With a flexible and scalable infrastructure, businesses can adapt to changing needs without significant disruptions or costly replacements. This future-proof approach ensures long-term investment value and prepares organizations for future security challenges. Cost-Effective Solution: When it comes to CCTV pricing, our integrated video surveillance and access control system offers exceptional value. Unlike traditional setups that require additional hardware and complex installations, our solution is cloud-based, eliminating the need for extensive infrastructure. With our system, all you need is a camera to capture footage, and everything else is seamlessly managed in the cloud with our Ultra App. This not only simplifies the setup process but also reduces costs, making it an affordable and convenient choice for organizations of all sizes. The integration of video surveillance and access control systems is a game-changer in modern security solutions. It provides a comprehensive and proactive approach to safeguarding premises, assets, and personnel. By combining real-time access control data with video intelligence, organizations gain unparalleled situational awareness, accurate identity verification, and streamlined operations. Moreover, the integration offers valuable forensic capabilities, operational efficiency, and future scalability. Embracing this powerful integration is not only good but imperative for organizations seeking robust and effective security solutions. Get in touch with us today to seize the full potential of video surveillance integration, bolstering your security stance and safeguarding what truly matters.
Gaining the Edge: 5 Key Advantages of Hosted Software

Hosted software, also known as Software as a Service (SaaS), offers a smart and cost-effective solution for businesses aiming to boost their efficiency and productivity. Five Compelling Reasons to Embrace Hosted Software: 1. Cost Savings: By eliminating the need for expensive hardware, software licenses, and IT infrastructure, hosted software ensures cost savings that empower growth. 2. Scalability: Addressing evolving business needs is seamless with hosted software, which effortlessly adapts to changes. 3. Accessibility: Ideal for remote or distributed workforces, hosted software allows access from anywhere with an internet connection. 4. Enhanced Security: Hosted software providers prioritize the latest security measures, safeguarding against cyber threats. 5. Seamless Integration: Streamline workflows by seamlessly integrating hosted software with other crucial business applications. In today’s technology-driven landscape, businesses of all sizes rely on software for streamlined operations and competitive edge. Yet, managing software can become costly and time-consuming. Enter hosted software solutions, a popular choice to overcome these challenges. For a reliable provider, consider the expertise of Millennium Group. Why Millennium Group Stands Out Unmatched Expertise: With over two decades of industry experience, Millennium Group excels in delivering top-tier hosted software solutions. Our dedicated experts constantly refine our products to meet the market’s evolving demands. Seamless Scalability: Adapting to business growth is effortless with our fully scalable hosted software solutions. Easily add or remove users, applications, and features to match your changing needs. Robust Security: Millennium Group prioritizes security, implementing rigorous measures to safeguard your data and systems. Our encrypted and regularly backed-up hosted software ensures unwavering protection. Cost-Efficiency: Eliminate the financial burden of in-house software management. Opt for Millennium Group’s hosted software and enjoy a predictable monthly fee covering all your software requirements. Tailored Support: At Millennium Group, personalized support is at the core of our service. We understand your unique needs and tailor solutions accordingly. Our dedicated support team remains ready to assist whenever needed. In conclusion, for a reliable, scalable, secure, and budget-friendly hosted software solution tailored to your specifications, trust Millennium Group. With extensive experience, unwavering expertise, and a commitment to customer satisfaction, we deliver the optimal solution for your business demands. Elevate your business with Millennium Group’s hosted software solutions today.
A Complete Guide on Access Control Systems

Access control systems are essential in today’s security landscape, providing a reliable way to protect physical spaces and sensitive data. Whether you’re managing a corporate office, a multifamily residential complex, or a healthcare facility, access control solutions offer a streamlined method for securing your premises, ensuring that only authorized individuals are granted access. This guide will explore everything you need to know about access control systems, their features, benefits, and how they can enhance security across various industries. What Are Access Control Systems? An access control system is a security solution used to regulate who can enter specific areas within a building, facility, or restricted zone. These systems ensure that only authorized personnel can enter certain locations, whether it’s an office, server room, or even a secure parking lot. By using authentication methods like keycards, biometrics, PIN codes, or mobile devices, access control solutions provide both physical and digital security. At its core, an access control system helps manage and monitor entry points, offering a high level of security while ensuring that access is granted only to those who have the proper credentials. Why Access Control Systems Matter 1. Reducing Security Risks As security threats continue to evolve, having a robust access control system is more important than ever. In today’s digital and physical world, traditional lock-and-key methods are no longer enough. Modern access control systems use multiple layers of authentication, such as biometric verification and smartcards, to protect against unauthorized entry. For instance, biometric methods like fingerprint or facial recognition are nearly impossible to bypass, offering a higher level of security than conventional PIN codes or keycards. This heightened security significantly reduces the risk of unauthorized access and strengthens overall safety. 2. Streamlining Entry and Exit In fast-paced environments, efficiency matters. Traditional methods of managing access—like physical keys—are slow and prone to human error. With access control solutions, the entry and exit process is fast, automated, and secure. Employees or visitors can access buildings or restricted areas within seconds using smartcards, biometric scans, or mobile devices. Additionally, many cloud-based access control systems integrate with time and attendance systems, allowing businesses to monitor employee hours and enhance operational efficiency. 3. Real-Time Access Monitoring One of the most significant advantages of modern access control systems is the ability to monitor access in real-time. Traditional locks don’t provide visibility into who is entering or leaving a space. However, with access control solutions, every entry and exit is tracked, complete with timestamps, locations, and user credentials. This real-time data allows administrators to quickly detect and respond to security incidents, such as unauthorized access or breached entry points. If a credential is lost or stolen, access can be revoked remotely and instantly, ensuring that your premises remain secure. 4. Flexible and Scalable Security Whether you’re managing a small office or overseeing a large multifamily property, access control systems offer scalability and flexibility. These systems can be easily customized to suit the security needs of any organization. For example, access permissions can be tailored for different users, specifying which areas they can enter and when. This flexibility is especially beneficial for industries that require strict access control, such as healthcare, education, and finance, where sensitive areas must be protected. Key Features of Access Control Systems 1. Authentication Methods The heart of any access control system is its authentication method, which verifies the identity of individuals attempting to enter a secure area. Several authentication methods exist, including: Keycards: Swiping or tapping a keycard at a designated reader grants access to authorized individuals. Biometric Scanning: Fingerprints, facial recognition, and retina scans provide highly secure, unique identifiers for everyone. PIN Codes: Personal identification numbers (PINs) offer a simple, secure method of authentication. Mobile Access: Users can gain access by using their smartphones, leveraging Bluetooth, NFC, or QR code technology. Each method has its benefits, allowing businesses to choose the most suitable solution for their security needs. 2. Control Panels The control panel is the nerve center of an access control system. It processes data from authentication devices (like keycard readers or biometric scanners), stores access credentials, and communicates with locking mechanisms to grant or deny entry. Many modern systems use cloud-based control panels, offering remote management capabilities. 3. Door Hardware The locking mechanism is a crucial component of any access control system. This can range from traditional mechanical locks to advanced electronic locks that can be integrated into the system for greater flexibility. Electronic locks are easier to control, can be remotely locked or unlocked, and are often more secure than traditional locks. 4. Software for Access Management The software component of an access control system allows administrators to manage user credentials, configure access settings, and generate detailed access logs. Many systems now offer cloud-based software that allows businesses to manage their access control remotely, from any location, at any time. 5. Integration with Other Security Systems Integrating cloud-based access control solutions with other security technologies, such as CCTV cameras, alarm systems, and fire detection systems, enhances the overall security infrastructure. For example, integrating access control with surveillance cameras allows businesses to monitor who enters and exits specific areas and verify their identity in real-time. Cloud-Based Access Control Solutions 1. Remote Access and Management Cloud-based access control systems are revolutionizing the way businesses manage security. These systems allow administrators to remotely monitor and manage access from anywhere in the world. This means you can view real-time activity, grant or revoke access, and adjust settings—all from your phone or computer. Cloud solutions also offer greater flexibility, as they don’t require on-site hardware, reducing maintenance costs and providing easier scalability. 2. Cost-Effectiveness and Scalability Cloud-based access control systems are often more cost-effective than traditional, on-premise systems. They eliminate the need for expensive servers and onsite infrastructure, and their scalability allows you to easily add new doors, users, or locations as your business grows. 3. Automatic Updates and Maintenance With cloud-based solutions, updates and maintenance are handled automatically, ensuring that your system always runs the latest software version with the
Revolutionizing the Digital Badging Capabilities in the Access Control Industry

In education, IT, healthcare, or any other industry, it’s vital to recognize and control who enters or exits a facility, however, the subjects of physical access control and identification badges can be a bit confounding. What is a badge entry system? It is an electronic building access control solution that approves access all through the facility utilizing an individual’s ID as the credential. In this way, the identification is utilized for both visual distinguishing proof and access approval. Accordingly, this kind of framework is well-known for industrial and commercial properties. You’ve probably seen badge entry systems previously. A lot of visual media depicts spies swiping ID cards to get to limited regions. But properties don’t need to have a highly classified status to fit the bill for a badge entry system! Properties like schools, college campuses, medical clinics, and places of business ordinarily use badge entry systems for security efforts. Users essentially swipe or scan their ID cards to get to a building and the rooms inside. The badge comes as both an actual card or a digital footprint on your cell phone – the last option comes with countless benefits over the previous one. The framework takes into account the production of custom printed access control credentials. This lets a solitary badge/card or cell phone act as both recognizable proof and access control validation eradicating the requirement for duplication of credentials. The Millennium Badge Module permits you to create and supply your photo ID badges. The badge module consists of several options to fit your needs: a software-controlled digital camera, a high-end imaging capture card, and powerful Ultra Software. Badges can include a bar code, digital signature, or barcoding compatible with our electronic access control systems. The Badging & Access System is very user-friendly and customizable to fit most applications. Data in the system comes from personnel records and identification cards issued by the Federal/State government. Features Of Badging and Identification License via activation Multiple columns and rows per layout Predefined templates Text, image, and drawing objects Ghosting images Image opacity ,asking Manual data entries 1D & 2D barcodes Export card preview Print to Windows printers Single and double-sided printing Import and export images Webcam support Camera support Magnetic coding Create user group profiles Assign/remove users(s) to/from groups Temporarily block user(s) Advanced fraud prevention mechanism Account password expiration feature Hide database information from user(s)/group(s) Hide card template from user (s)/group(s) Benefits of Using Millennium as Badging and Identification Partner Easy Badging Process: Badging module makes the whole process easy. The administrator or operator can place the photo on the already finalized company template in a matter of a few seconds. Further, entry-related data can be copied from the employee’s database. Digital ID – Mobile Identification: Millennium presents a Digital ID that allows the cardholder to carry a digital card on his mobile phone. It can be issued in the form of PDF, JPEG, PNG, etc. instead of carrying a plastic card every time. Safeguard access to your sensitive areas/data: To safeguard access to your premises and/or your data, the employee badge can take on the function of an access control card. This allows you to prevent intrusions by unauthorized persons and, at the same time, protect your employees, infrastructure, property, and data. By adding a barcode, QR code, or direct encoding in the card to the badge, you can easily manage access to your buildings, sensitive zones, and data using the permissions and rights that you define. Default/Custom ID Badge Templates: Millennium has by-default many ID badge templates that you can use for your employees, visitors, contractors, or dealers. Custom-made ID badge templates are also available which makes the system very easy to learn. Read More: All you Need to Know About Access Control System – A Complete Guide Establish a More Professional Image of your Company Portray the colors of your company and strengthen the emotion of belonging with a personalized worker badge developed in line with your company s visual identity. Create: Design your ID card designs through different shapes, font sizes, barcodes, etc Search & Sorting: With the quick search option, get the required data from the cluster in no time and in a precise way. Photo Capture: Take photos utilizing face recognition, auto cropping, and other useful tools. Interface: An interactive and easy-to-use interface that both freshers and experienced graphic designers can use. Placeholder: Use placeholders to smoothly allocate the photo, company logo, barcode, and signature. Conclusion The well-established legacy of a physical keycard for identification being more unassailable than a digital keycard is no longer accurate. Mobile security has grown, and the security exposures of a physical keycard, which can be easily misplaced or cloned, still stay. Similarly, mobile badging provides pervasive, comprehensive security and a personalized experience across all of a company’s platforms, whether on a browser or mobile. While there will still be a role for the physical ID badge, Millennium Ultra has determined to enhance it by offering it a digital twin with features and specifications that other badging companies simply don’t offer.